Summary
In a previous post I wrote about loading to the trusted root store on Windows Web Apps inside ASE, in order to trust privately issued certs. This is required if you connect over SSL to internal endpoints using privately issue certs, or make connections between sites in that ASE and use a private CA cert for the HTTPS binding.
Here I’ll share some comments that should help achieve a similar thing on Linux sites.
The reason for this post is to co-locate and explain a few important points about this setup which are a bit unclear.
Disclaimer: this is written based only on my personal understanding of the public facing documentation and commentary.
Various docs
- https://learn.microsoft.com/en-us/azure/app-service/configure-ssl-certificate-in-code#load-certificate-in-linuxwindows-containers
- Basic overview of how it works and where the certs go, some code examples, may not explain everything a person needs to know
- https://azure.github.io/AppService/2021/06/22/Root-CA-on-App-Service-Guide.html#linux
- Good explanation of Root CAs on App Service overall, multitenant and ASE
- https://github.com/MicrosoftDocs/azure-docs/issues/19305
- Various commentary and feedback on the scenario, some examples shared
How to
On Windows sites, this is relatively simple. Certs are loaded directly to the root store of the Windows VM and everything works as expected.
On Linux sites, it works fundamentally a bit different. The certs are made available to the VM as files in the directories mentioned on the documentation:
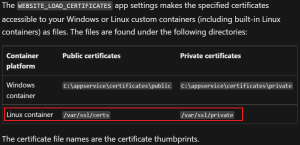
To load a cert for the private CA, the process should be a typical approach depending on the image used. Nothing particularly special happens here on App Service.
Debian based images (like Ubuntu) can follow a similar approach to what is described here: https://superuser.com/questions/437330/how-do-you-add-a-certificate-authority-ca-to-ubuntu.
Steps:
- First, the root CA and intermediates must be exported in an appropriate file type, Azure Portal accepts pfx and crt/cer.
- Upload the root CA and intermediate directly to the Web App via the Azure Portal or script
- Use the App Setting WEBSITE_LOAD_CERTIFICATES with value of * or the cert thumbprint values, to load the certificates as files to the directories mentioned in the documentation
- Use a startup script to update the root store of the container:
- https://learn.microsoft.com/en-us/azure/app-service/configure-common?tabs=portal#configure-general-settings
openssl x509 -inform der -in /var/ssl/certs/Public-CA-cert-GUID-Loaded-Portal.der -outform pem -out /usr/local/share/ca-certificates/Internal-CA.crt
update-ca-certificates- This script will need to be changed depending on how many certs need to be loaded, and the filenames you find.
- Alternatively, this can be achieved in site code as described in the github post and documentation.
Good luck!