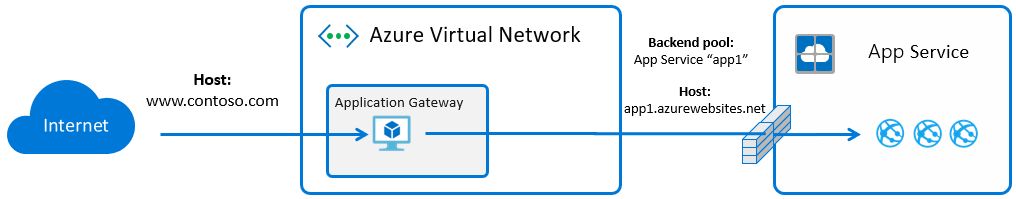
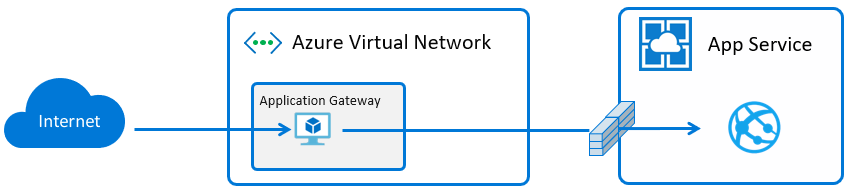
Summary
In a previous post I wrote about loading to the trusted root store on Windows Web Apps inside ASE, in order to trust privately issued certs. This is required if you connect over SSL to internal endpoints using privately issue certs, or make connections between sites in that ASE and use a private CA cert for the HTTPS binding.
Here I’ll share some comments that should help achieve a similar thing on Linux sites.
The reason for this post is to co-locate and explain a few important points about this setup which are a bit unclear.